Edge to Cloud Security: A Comprehensive Guide
As organizations increasingly adopt edge computing and cloud solutions, the convergence of these technologies has introduced new challenges and opportunities in cybersecurity. Edge computing, which brings computation closer to data sources, and cloud computing, which offers scalable and flexible resources, both play crucial roles in modern IT infrastructure. However, securing the interaction between edge devices and cloud environments is paramount to protect data, ensure compliance, and maintain operational integrity. According to Edge Market Insights Inc. report, the edge security market worth of USD 24 Bn in 2024 and expected to reach USD 174 Bn in year 2034 with CAGR of 21.9%. In this blog, we will explore the key concepts, challenges, and best practices for securing the edge-to-cloud continuum.
Understanding Edge to Cloud Computing
Edge Computing
Cloud Computing
The Convergence
Cloud
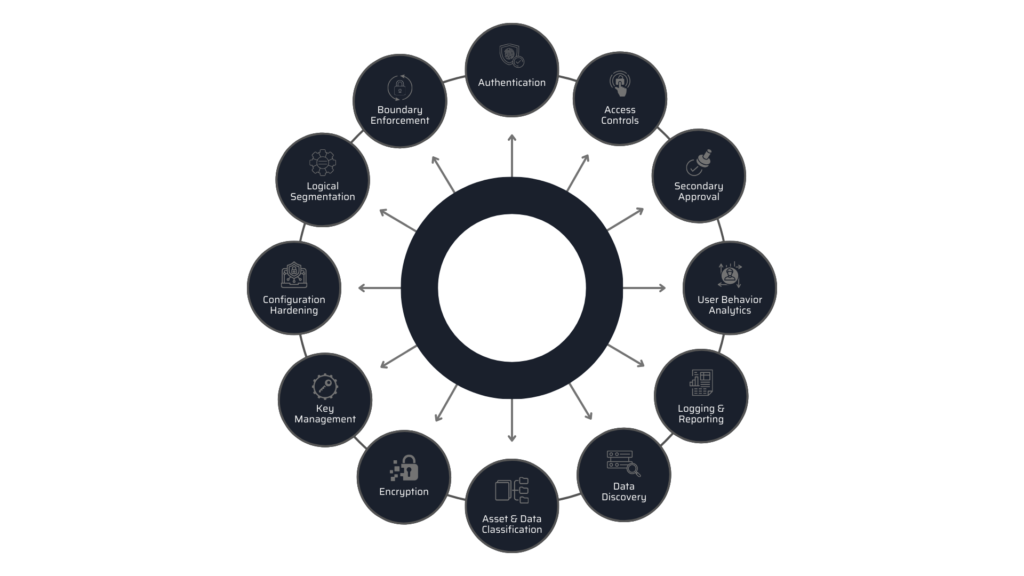
- Security Analytics and Visualization Platform (SAVP)
- Device Security Lifecycle Management
- Intrusion Detection Software (IDS)
- Identity & Access Management
- Filtering Engine
- Centralized Security Manager
Network
- TLS, Isolated Communication Channels
Edge
- Trusted Platform module (TPM)
- Trusted Execution Environment
- Chip with Trust Zone
- Root of Trust
Cyber Security Challenges in Edge-to-Cloud Architectures
Distributed Attack Surface
Data Integrity and Privacy
Resource Constraints
Diverse Environments
Compliance and Regulatory Requirements
Best Practices for Cyber Security Solutions
Implement Zero Trust Architecture
Strong Encryption
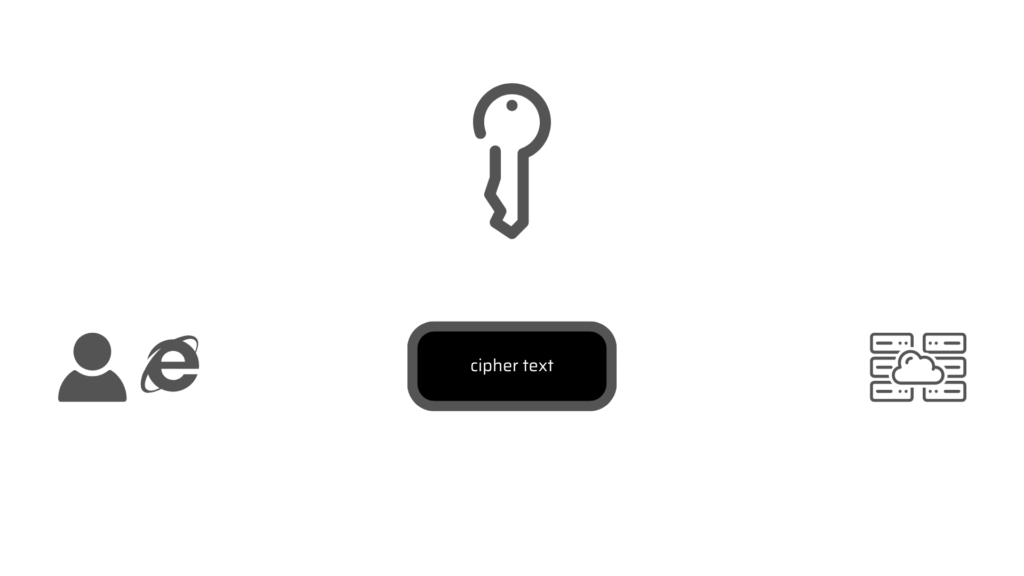
Network security using encryption and decryption
Secure Boot and Firmware Integrity
Implement secure boot mechanisms on edge devices to ensure that only trusted firmware and software can run. Regularly verify the integrity of firmware to prevent unauthorized modifications.
- Secure boot
- OPTEE (Trusted Execution Environment)
- TPM (Trusted Platform Module)
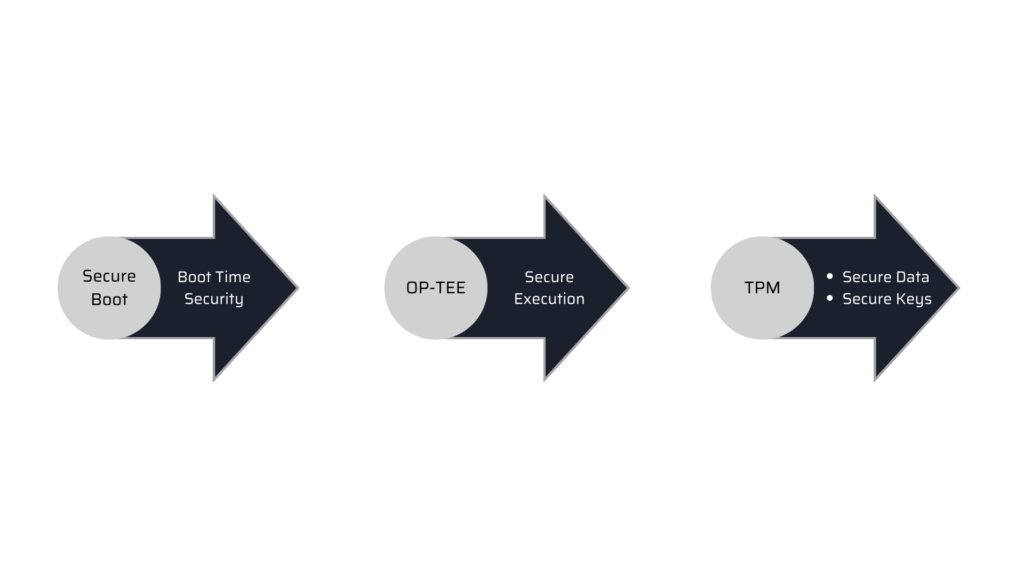
1. OPTEE / TEE:
Isolation – The TEE isolates itself from the non-secure operating system and uses fundamental hardware assistance to protect the installed Trusted Applications (TAs) from one another.
Small footprint – The TEE should be small enough to fit within an acceptable quantity of on-chip memory.
Portability – The TEE aims at being easily pluggable to different architectures and available HW and must support various setups such as multiple client OSes or multiple TEEs.
2. TPM:
The Trusted Platform Module (TPM) is a special purpose microcontroller designed by the Trusted Computing Group, which interfaces with a standard hardware/software platform to allow it to be secured to support the needs of only one party: the system designer.
It is used to securely create and store cryptographic keys, and to confirm that the operating system and firmware on your device are what they’re supposed to be and haven’t been tampered with.
The TPM 2.0 standard enables manufacturers such as Intel and AMD to integrate TPM capabilities with their chipsets instead of necessitating a separate chip.
Identity and Access Management (IAM)
Deploy robust IAM solutions that enforce strict access controls based on roles, permissions, and context. Ensure that only authorized entities can access critical resources in both edge and cloud environments.
Microsoft Azure and AWS are providing services for IAM solutions.
- Microsoft Azure Entra I
- AWS Identity and Access Management (IAM)
Patch Management and Updates
Regularly update edge devices and cloud components with the latest security patches to protect against known vulnerabilities. Automated update mechanisms can help ensure timely patching without disrupting operations.
- Azure Update Manager
- AWS Systems Manager Patch Manager
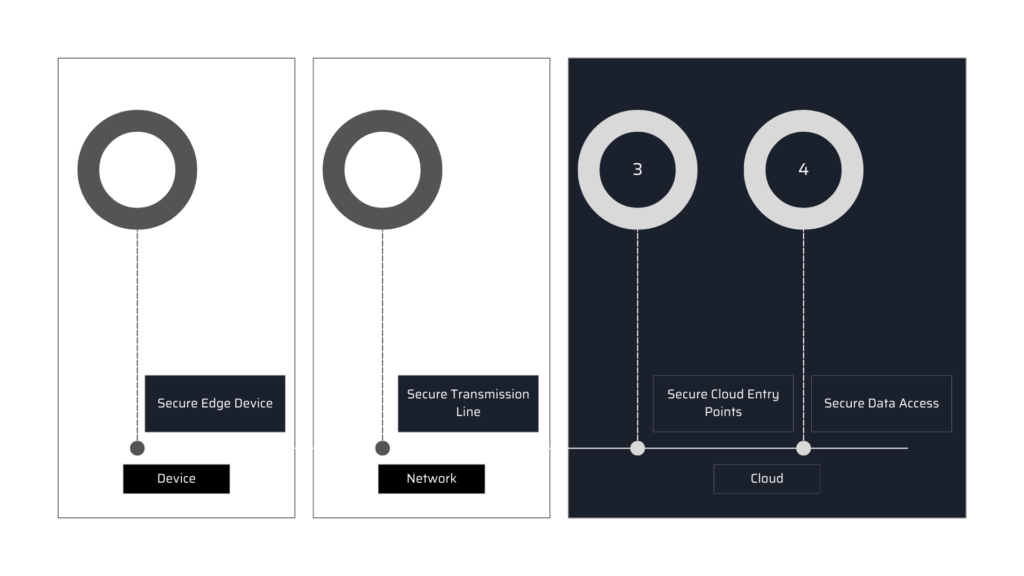
Network Segmentation
Use network segmentation to isolate critical systems and reduce the risk of lateral movement by attackers. Edge devices should be placed in secure zones with limited access to the cloud.
Below is the reference flow for cloud network segmentation:
Monitoring and Incident Response
Implement continuous monitoring of edge devices and cloud services to detect suspicious activity early. Develop an incident response plan tailored to the specific challenges of the edge-to-cloud environment.
Microsoft Azure offers a variety of services for threat monitoring and incident response, including:
- Security Operations Centre (SOC) Service: Provides threat detection and monitoring, incident response, and more.
- Microsoft Defender for Storage: Detects attempts to access or exploit storage accounts and provides security alerts with steps to mitigate threats.
- Microsoft Defender for Cloud: Provides threat protection for Azure workloads, as well as other clouds and on-premises environments.
- Microsoft Sentinel: A cloud-native SIEM solution that uses AI, security analytics, and custom alert rules to collect, detect, investigate, and respond to threats in real time.
Data Minimization
Reduce the amount of sensitive data stored or processed at the edge. Only transmit necessary data to the cloud and anonymize or tokenize sensitive information wherever possible.
Real-World Applications
Smart Cities: Cyber security in smart cities covers various use cases to boost urban safety and resilience. Protecting critical infrastructure like water and electricity networks is crucial against cyber threats that may disrupt services. Smart traffic management systems also benefit from secure data transmission between vehicles and control centers, reducing accident risks and improving traffic flow efficiency.
Industrial IoT: Cyber security in Industrial IoT (IIoT) is essential for safeguarding critical data and intellectual property, protecting against unauthorized access and data breaches. This comprehensive security approach ensures that all communication channels are encrypted, reducing vulnerabilities across the system. Also, strengthens IIoT resilience by enabling quick detection and response to potential cyber threats, ensuring operational stability and uninterrupted service. With these protections, IIoT environments maintain high levels of integrity and trust, which is crucial for sensitive industrial applications.
Healthcare: In healthcare, cyber security is essential to safeguard sensitive patient data throughout the entire ecosystem, from medical devices to cloud storage. This approach ensures that data is encrypted and shielded from unauthorized access at every stage, maintaining patient confidentiality and data integrity. By implementing comprehensive encryption, access controls, and real-time threat detection, end-to-end security mitigates the risk of data breaches and cyberattacks, creating a robust line of defense in healthcare’s digital landscape.
The Future of Edge-to-Cloud Security
As the adoption of edge computing and cloud technologies grow, so will the sophistication of cyber threats targeting these environments. Emerging technologies such as AI-driven security, blockchain, and quantum cryptography are expected to play significant roles in enhancing edge-to-cloud security. Organizations must remain vigilant, continuously adapt their security strategies, and invest in new technologies to protect their edge-to-cloud infrastructure against evolving threats.
All in all, in a connected world, robust edge-to-cloud security is vital as organizations adopt decentralized architectures. At MosChip, we leverage new-age technologies while safeguarding organization data, operations, and reputation. By understanding the unique security challenges and implementing best practices, MosChip can build a resilient and secure edge-to-cloud architecture.