Getting started with RISC-V and its Architecture
Due to high computing demands, SoCs are becoming more complex. Machine Learning, Multimedia, connectivity are critical factors for this. When developing SoC, the critical decision to be made is choosing the proper Instruction Set Architecture (ISA) and the processor hardware architecture. There are many ISA available having different pros and cons. Some of them are proprietary and licensable, while some of them are open. ARM and Intel are two populate players in processor architectures.
There are different variants of architectures provided by vendors. Significant benefits of using licensed architecture are already developed software and ready to use ecosystem. However, design flexibility is minimal with these architectures. Open-source ISA offers greater flexibility, and they are free. Having an open-source also makes room for continuous improvements. People can modify them as per their requirements and contribute back to make them better.
RISC-V (Reduced Instruction Set Computing) is an open standard instruction set architecture based on Reduced Instruction Set Computing (RISC) principles. The RISC-V architecture project was started in 2010 by Prof. Krste Asanović, Prof. David Patterson, graduate students Yunsup Lee and Andrew Waterman at the UC (University of California, Berkeley).
RISC-V is a royalty-free, license-free, and high-quality based ISA sets. The RISC-V standards are maintained by the RISC-V Foundation Company. The RISC-V Foundation is a non-profit organization formed in Aug 2015 to maintain its standards publicly. Currently, more the 230+ companies have been joined the RISC-V Foundation. The RISC-V is freely available under the BSD license. Well, the RISC-V is neither a company nor a CPU implementation.
How RISC-V is different than other processors?
Freely available
Unlike other ISA designs, the RISC-V ISA is provided under free licensing, which means that without paying any fees, we can still use, modify, and distribute the same.
Open Source
As RISC-V ISA is open source, people can use them and improve them. This makes the product more reliable.
Fully Customizable
Though there may be different proprietary processor cores, customization is not possible based on the requirement. The advantage of using the RISC-V ISA (Instruction Set Architecture) is that it enables companies to develop a completely customizable product, specifically to their requirements. They can start with the RISC-V core and add whatever is based on their need. This ultimately saves their time and money, resulting in low cost and low power products which can be used for a long time.
Support for user-level ISA extensions
RISC-V is very modular. There are many standard extensions available for specific purposes which can be added to the base as per requirement. Developers can also create their non-standard extensions. Some of the standard extensions used by RISC-V are:
- M – Integer Multiplication and Division
- I – Integer
- A – Atomics Operation
- F – Single-Precision Floating Point
- D – Double-Precision Floating Point
- Q – Quad-Precision Floating Point
- G – General Purpose, i.e., IMAFD
- C – 16-bit Compressed instructions
Designed 32/64/128 bits wide support
RISC-V has different bits width support providing more flexibility for the product development.
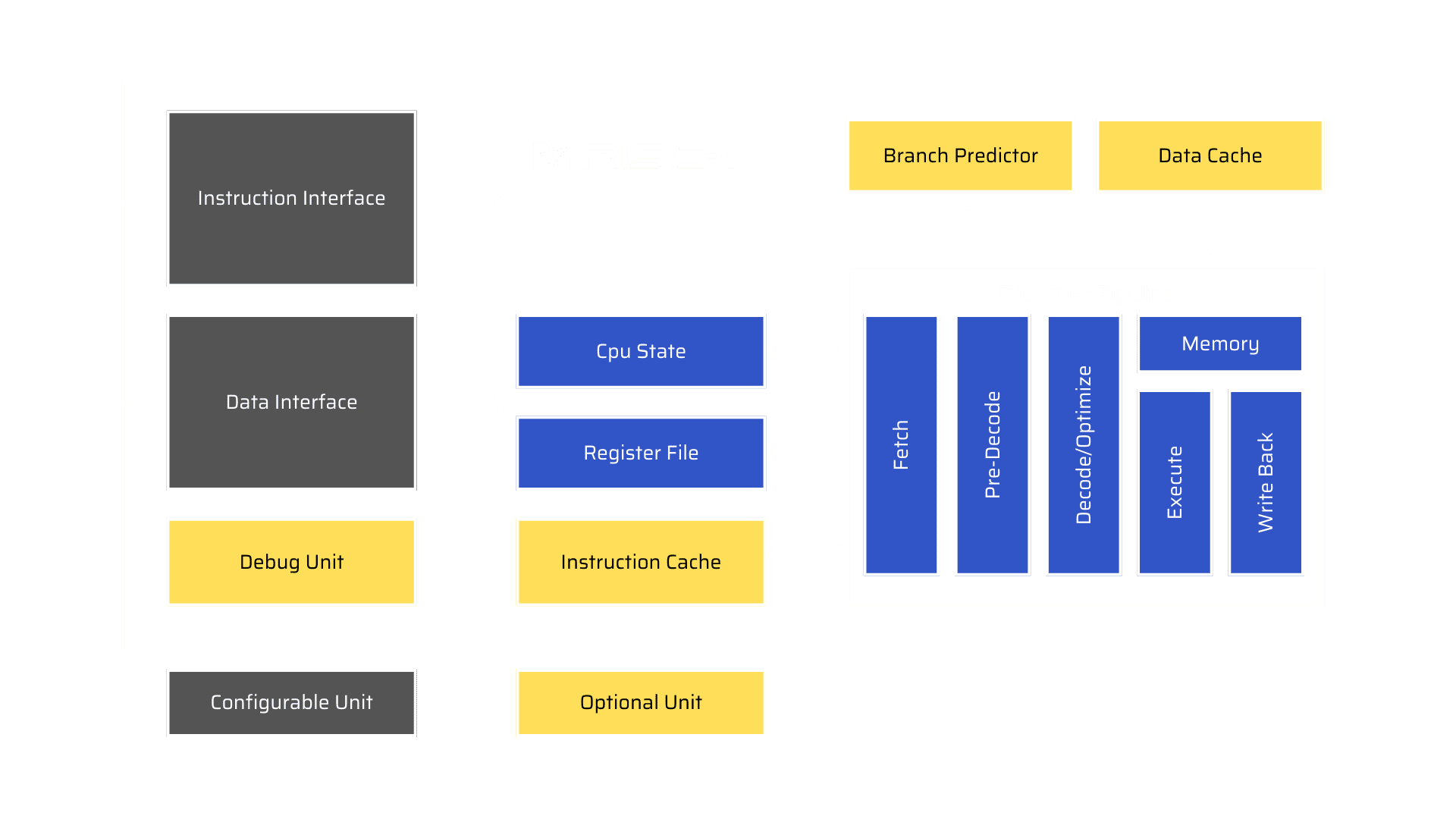


Riscv processor
Apart from the above benefits, RISC-V has many vital features like multicore support, fully virtualizable for hypervisor development.
The RISC-V supports different software privileged levels
- User Mode (U-Mode) – Generally runs user processes
- Supervisor Mode (S-Mode) – Kernel (Including kernel modules and device drivers), Hypervisor
- Machine Mode (M-Mode) – Bootloader and Firmware
The processor can run in only of the privilege modes at a time. The machine mode is the highest privileged mode and the only required mode. The privilege level defines the capabilities of the running software during its execution. This different level of models makes RISC-V a choice for certain & safety products.
One thing to note is RISC-V is open-source Instruction Set Architecture. Using this architecture, anybody can develop processor cores. Developed core can be free or proprietary depending on the choice of who develops it.
RISC-V can be used for a variety of applications because of its great flexibility, extensions, and possible customization. The RISC-V is suitable for all types of micro-processing systems to the super-computing system. It can fit into small memory devices consuming less memory & power. Similarly, its other variant can provide high computing capabilities. Its privileged modes can provide security features like trust zone & secure monitor calls.
Some of the applications suited for RISC-V are:
- Machine Learning edge inference
- Security solutions
- IoT
RISC-V for Security Solution
MosChip is using Lattice Semiconductor RISC-V MC CPU soft IP to develop security solutions. The below diagram illustrates it in brief.
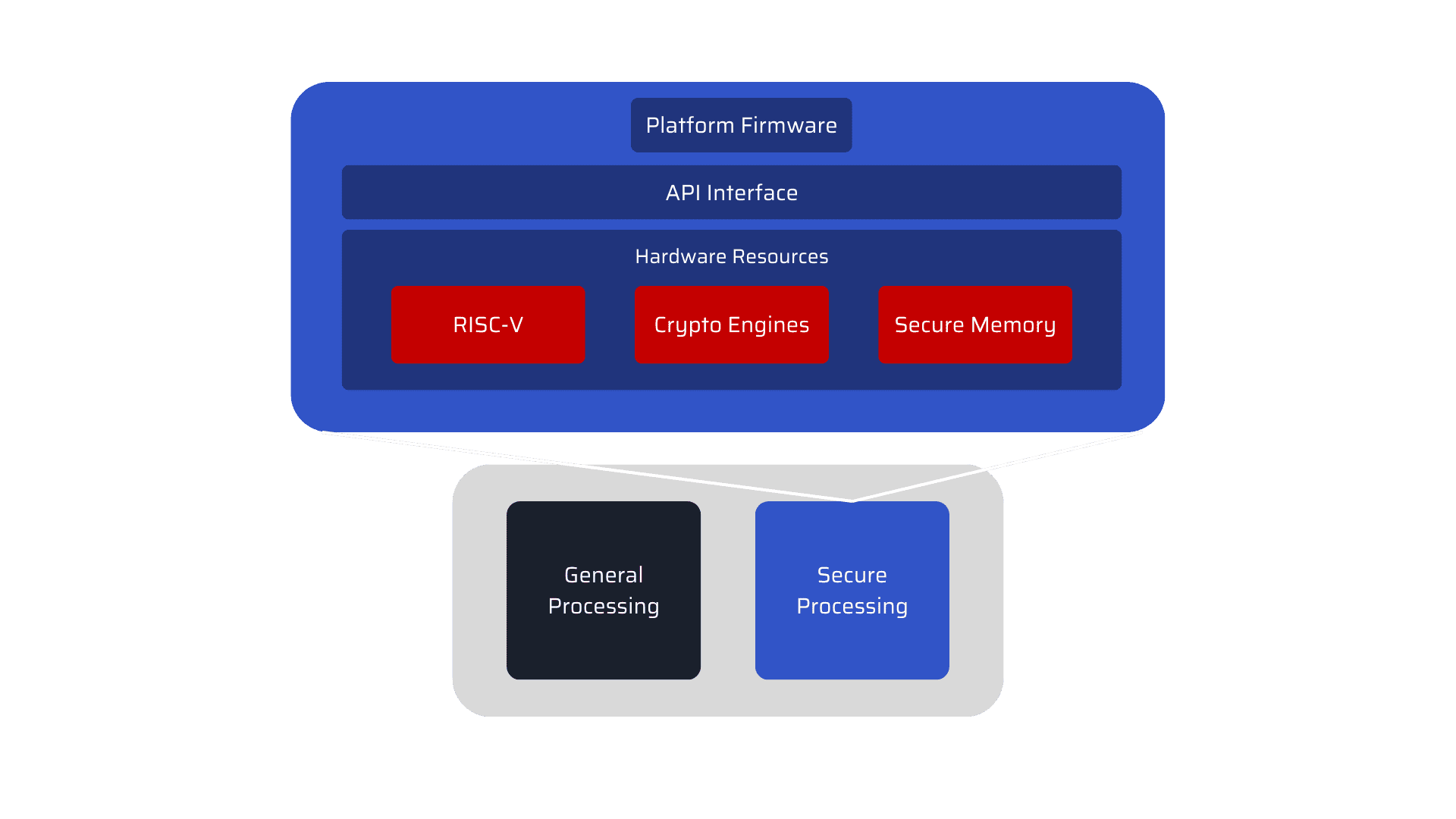


 Security solution
Security solution
In Safety-critical products, RISC-V works as the root of trust to ensure the authenticity and integrity of the firmware. It provides below functionalities:
- Protect platform firmware & critical data : It protects platform firmware and critical data from unauthorized access.
- Ensure authenticity & integrity of Firmware : On the boot, it checks for firmware signature and verifies that it is not tempered.
- Detect corrupted platform firmware & critical data : It checks platform firmware & critical data on boot and runtime when requested. If the platform or critical data gets corrupted for any reason, it can detect them and take corrective actions.
- Restore corrupted platform firmware and/or critical data : If platform firmware or critical data are corrupted, it performs restoration of platform firmware and/or critical data from the backup partition based on the requirement.
- Runtime monitoring for unintended access : During runtime, it monitors bus traffic accessing secure memories (e.g., SPI traffic) and blocks unintended access.
RISC-V for IoT solution
Gateway is developed with the RISC-V-based MCU to leverage the security features provided by RISC-V.
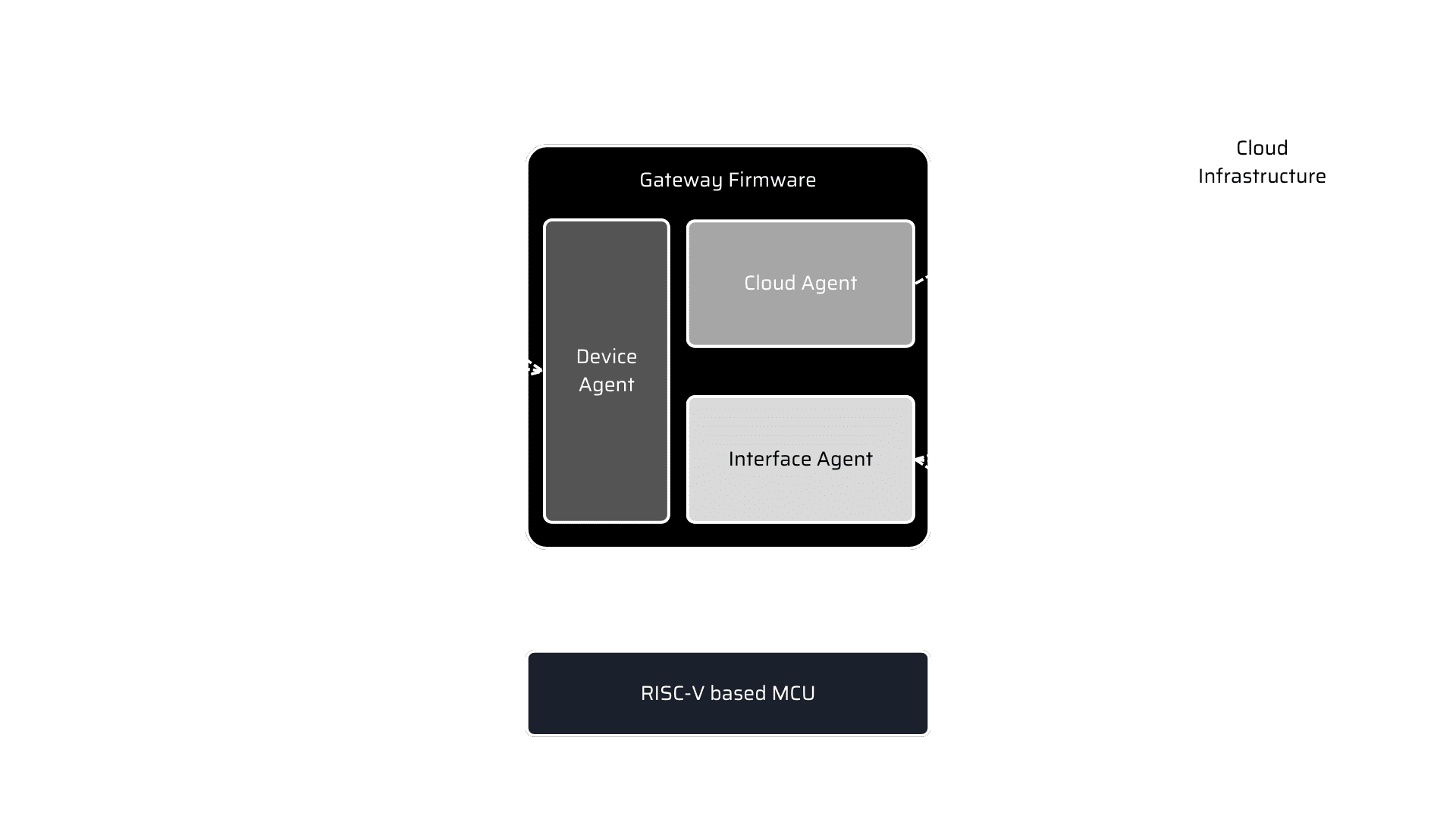




 Riscv IoT solution
Riscv IoT solution
The gateway is developed to perform device management, user management, and services management. A cloud agent is developed to handle all the cloud activity from device to cloud via gateway. A device agent is developed to manage all the devices connected to the gateway. A service agent makes sure all the interface and status of the interface and connected device.
About MosChip:
MosChip has 20+ years of experience in Semiconductor, Embedded Systems & Software Design, and Product Engineering services with the strength of 1300+ engineers.
Established in 1999, MosChip has development centers in Hyderabad, Bangalore, Pune, and Ahmedabad (India) and a branch office in Santa Clara, USA. Our embedded expertise involves platform enablement (FPGA/ ASIC/ SoC/ processors), firmware and driver development, BSP and board bring-up, OS porting, middleware integration, product re-engineering and sustenance, device and embedded testing, test automation, IoT, AIML solution design and more. Our semiconductor offerings involve silicon design, verification, validation, and turnkey ASIC services. We are also a TSMC DCA (Design Center Alliance) Partner.
Stay current with the latest MosChip updates via LinkedIn, Twitter, FaceBook, Instagram, and YouTube








